Prevent cyber attacks and stay compliant with
Non-Stop Cyber Security Validation
Stop overpaying for one-off penetration tests. Our continuous security validation service keeps your business ahead of emerging threats without breaking the bank.
-
Fulfills compliance requirements for penetration testing
-
Developed by CHECK certified security professionals
-
Same-day setup, no deployment burden, transparent pricing
A Managed Service with an Immediate ROI
Effortlessly enhance your cyber security while maximizing cost savings and efficiency.
Always On, Always Secure
Your business operates non-stop, and your cyber security framework should too. Our Continuous Security Validation service improves on traditional approaches to security testing to bring you 24/7 coverage, ensuring that your digital infrastructure is constantly monitored and continuously fortified against emerging threats.
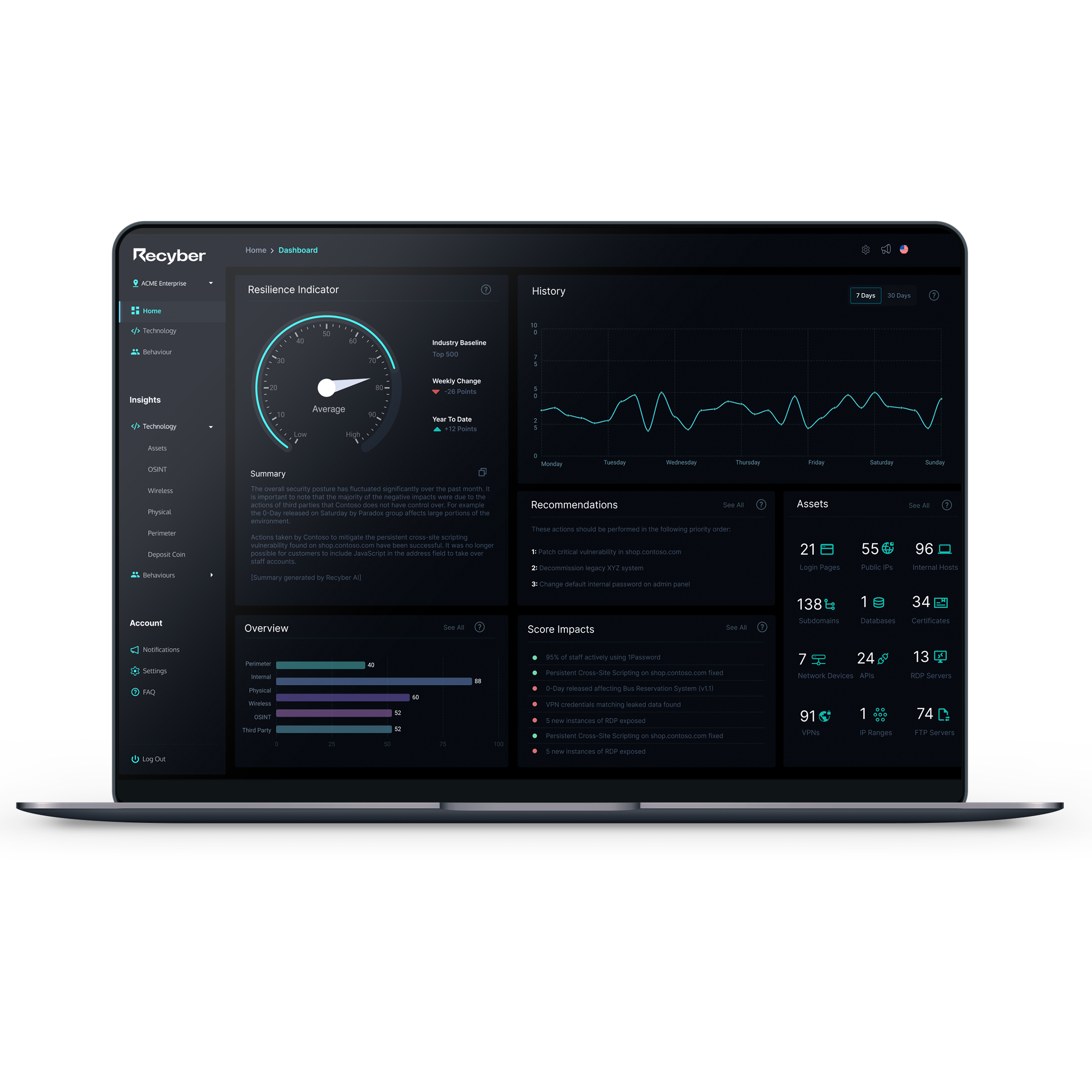
Navigate Cyber Risk with Confidence
Delivered through an easy-to-use dashboard and backed by a team of certified ethical hackers, the Recyber Platform identifies threats and vulnerabilities before attackers have a chance to exploit them.
Cut Through The Noise
Review intelligently prioritises high severity vulnerabilities so your team can streamline remediation efforts.
Remediation Guidance
Review supports remediation efforts with tailored guidance from our team of certified security experts.
Correlate Human Behaviour with Technical Risks
Review intelligently integrates data feeds from Republic endpoints to correlate human risk with technical vulnerabilities.
Continuous scanning that establishes a baseline of expected services and behaviours. Changes that deviate from the usual patterns are flagged for review by our certified team of penetration testing experts.
Our service embraces an "unlimited scope" approach, ensuring that every aspect of your digital presence is viewed through the same lens as a real attacker.
Real-time, interactive reporting that provides not only an instant snapshot of your security posture but also allows for dynamic updates as vulnerabilities are identified and resolved.
Our risk scoring algorithms ensure that your team isn't bogged down by false positives or low-impact issues. Instead, you can focus your resources and efforts on addressing critical vulnerabilities, ensuring optimal security and peace of mind.
Improving on Legacy Approaches
Traditional penetration testing, vulnerability scanning, and attack surface management systems have failed to keep pace with the sophistication of modern attackers and the complexity of modern IT networks. As a result, businesses often grapple with inflated costs of outdated methodologies and receive a false sense of security from vendors, remaining blind to the latent threats that modern adversaries can exploit with ease.
Our platform merges the best aspects of traditional security testing while eliminating their inefficiencies. With an intelligent blend of automation and human-led expertise, our solution fixes the following issues associated with conventional approaches to security validation:
As the cost of cyber crime continues to soar, the need for high quality, continuous cyber risk assessments has never been greater. (sources: Stastica, FBI, IMF)
Traditional penetration testing engagements are often constrained by a limited timeframe, typically ranging from a few days to a couple of weeks. This approach can lead to incomplete assessments, potentially leaving undiscovered vulnerabilities. In real-world scenarios, cyber attackers are not confined by such constraints; they can patiently probe systems over extended periods until they find weaknesses. A time-limited view can also fail to adapt to the dynamic nature of the ever-evolving network environments. With emerging threats and rapid technological changes, a once-a-year or biannual penetration test can leave organizations with a false sense of security.
A common limitation of traditional penetration tests is the restriction imposed by the scope defined by the client.
While the intent is to focus on areas perceived as vulnerable, this often means that only specific portions of a network or particular systems are tested, leaving the rest unchecked. This approach relies heavily on the client's ability to accurately identify and prioritize their most critical assets, but the reality is that many organizations may not have complete visibility or understanding of their entire digital landscape.
As a result, significant vulnerabilities in out-of-scope areas can go unnoticed, providing cyber attackers with potential entry points that remain unchecked. True security assessment should offer a holistic view of the entire network environment, ensuring that no stone is left unturned and that organizations can feel confident in their overall security posture.
Traditional penetration testing often comes with a hefty price tag. The financial strain arises not only from hiring specialized consultants but also from the day-rate model typically employed in the industry. This model charges clients based on the number of days a team dedicates to testing, rather than the results they produce. This can lead to spiraling costs, especially when engagements extend due to unforeseen complexities or when additional areas of interest are identified during the assessment. Furthermore, the necessity for periodic retesting to account for new vulnerabilities or system changes exacerbates these costs over time. While organizations undoubtedly understand the importance of ensuring their cyber defenses are robust, many are left grappling with how to balance these vital security measures against their budget constraints. In an era where cyber threats are evolving rapidly, it's essential for businesses to have access to cost-effective and comprehensive security assessments that don't compromise on depth or quality.
The reliance on PDF reports as a primary means of communicating findings post-penetration testing has become a significant bottleneck in the realm of cyber security.
These reports are often bulky, spanning hundreds of pages, making it challenging for IT and security teams to parse and prioritize the actual threats. While they might be comprehensive, the static nature of a PDF means that actionable insights are buried under layers of information, and they lack the dynamic interactivity required for a modern remediation workflow. Moreover, these reports can quickly become outdated, given the ever-evolving nature of cyber threats and the rapid pace of organizational changes.
Navigating through a dense PDF to pinpoint high-priority vulnerabilities can consume precious time and resources. This archaic method of reporting fails to provide organizations with a real-time, interactive view of their threat landscape, potentially leaving them vulnerable to emerging threats while they sift through pages of data. In today's fast-paced digital world, organizations need agile, streamlined, and interactive reporting mechanisms that facilitate rapid response and remediation.
One of the most prevalent challenges in penetration testing is the occurrence of false positives. A false positive refers to a situation where a security tool or test reports a vulnerability that, in reality, doesn't pose an actual threat to the system. These can be particularly troublesome for several reasons. Firstly, addressing false positives consumes valuable time and resources that security teams could otherwise utilize to mitigate genuine threats. This can divert attention away from real vulnerabilities, potentially leaving critical systems exposed. Secondly, an abundance of false positives can lead to 'alert fatigue.' Security professionals, overwhelmed by a barrage of alarms, might become desensitized, increasing the likelihood of overlooking a genuine threat. Moreover, a consistent stream of false positives can erode confidence in security tools and processes, potentially causing stakeholders to question the validity of other findings, even when they're accurate. To combat the issue of false positives, it's imperative to employ rigorous validation processes, combined with a discerning human touch, ensuring that identified vulnerabilities are genuine and prioritized appropriately.
One of the intrinsic challenges with traditional penetration testing is the issue of repeatability. Traditional pen tests are often seen as a snapshot in time, offering a glimpse of the vulnerabilities present during a particular test window. However, systems, configurations, and applications evolve constantly. What was secure two months ago might not necessarily be secure today due to newly discovered vulnerabilities, changes in configurations, or system updates. With this dynamic environment, a single penetration test might miss vulnerabilities introduced shortly after or become outdated quickly. Without repeatability, companies might have a false sense of security, thinking they are protected based on the results of a single test. This challenges organizations to constantly re-test, incurring additional costs and time. A truly resilient security posture requires ongoing assessments, continuous monitoring, and the ability to repeatedly test systems as they evolve. The ephemeral nature of a one-off penetration test may not capture this need for consistent security validation, making repeatability a critical concern.
How it Works
From seamless onboarding to continuous, proactive threat monitoring, discover our step-by-step

“It’s the first time I’ve seen the results of a penetration test presented like this. Very simple to setup and has given us a new perspective on our security posture. We were able to quickly identify a critical attack path that previous pentest vendors had missed. Overall, a great outcome for us that speaks volumes about the power of this new approach."
-CISO of a 13,000 seat global commodity trading company
Frequently Asked Questions
No, our security validation service is designed to be non-intrusive, operating efficiently in the background to ensure your business operations continue smoothly.
No, there is nothing for you to do after the purchase. We'll use the domain from your email address to start mapping your organisation's digital footprint, and will send you a link to login once the initial results are ready.
Yes, if your organisation has special requirements or security preferences, please contact our sales team before purchase to arrange for customisable scanning options.
Think of traditional penetration testing like an annual health check-up: it's useful, but it only tells you about your security on that specific day. A lot can happen in between those check-ups. Our service, on the other hand, is like having a continuous health monitor that checks your system's security every single day. This way, if a new threat appears or something changes, we catch it immediately, not just once a year. It's a constant, vigilant approach to keeping your business secure in the ever-changing digital world.
Most compliance standards require some form regularly scheduled penetration testing or cyber security assessment. A subscription to our Continuous Security Validation service fulfills this requirement by testing your infrastructure on a daily basis.
We provide real-time alerts and detailed remediation guidance directly through the platform dashboard. When highly critical alerts are raised, we typically reach out directly to the point of contact on your account.
Get Started Today
Cyber criminals don’t stop, and neither should your security testing. With our managed service, you’re not just getting cutting-edge security; you’re securing peace of mind.
Business Benefits
Reputational Safeguarding
A single attack can severely damage your brand and ultimately, your bottom line. Our service protects your business by identifying and addressing vulnerabilities before attackers have the chance to exploit them.
Regulatory Compliance
Our service exceeds compliance requirements for annual security testing by assessing your digital infrastructure on a daily basis.
Cost Effective Security
With our small business package, you get the sophistication of an enterprise-grade security solution without the hefty price tag.
£2,400/year
Billed Annually
Small Business Package
Continuous Security Validation Subscription
Advanced Monitoring: 12 months of continuous cyber security validation, proactive threat monitoring, and expert-guided ethical hacking.
-
Dedicated Platform Access
-
Continuous Toolkit Updates
-
Access to Customer Support

